Category: Security
-
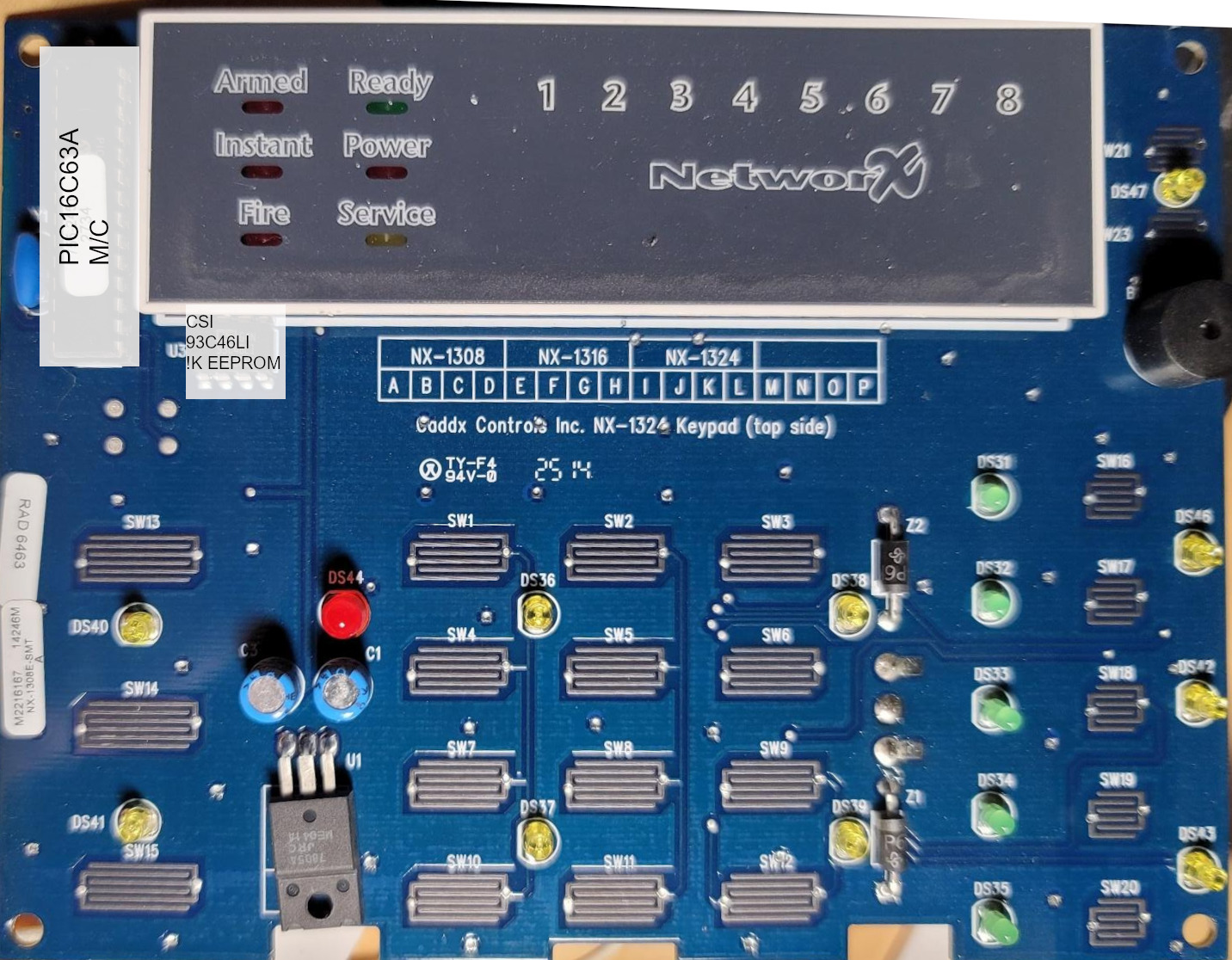
Alarm System Part 4: The Keypad
This Blog is part of a Series! Check out the rest if you haven’t already: At this point, I’ve dumped the EEPROM off the panel, and discovered that there can be some data stored in the PIC Microcontroller on the panel as well. The datasheet for that is >300 pages, so I’m not planning on…
-
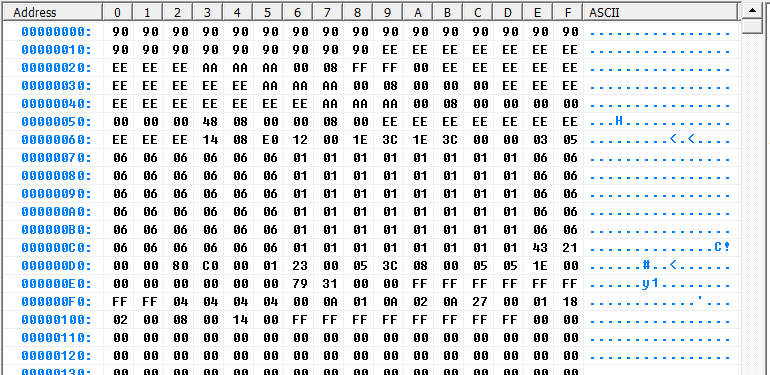
Alarm System Part 3: Security System – Dumping the EEPROM
If you’re coming here looking for the dump, I can’t share it. I don’t know what the laws are on this and it feels pretty DMCA-ish. Sorry. This Blog is part of a Series! Check out the rest if you haven’t already: So, the EEPROM programmer arrived today. For that, I’m excited. And nothing warms…
-
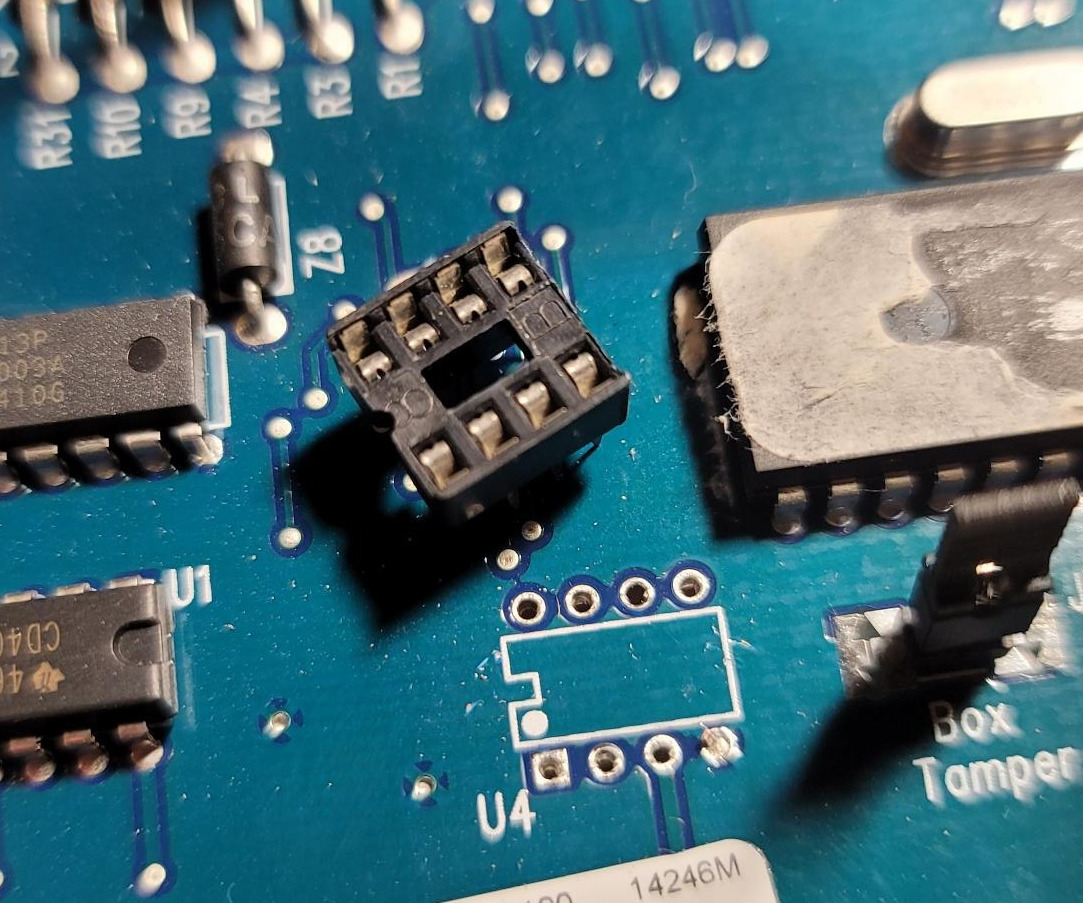
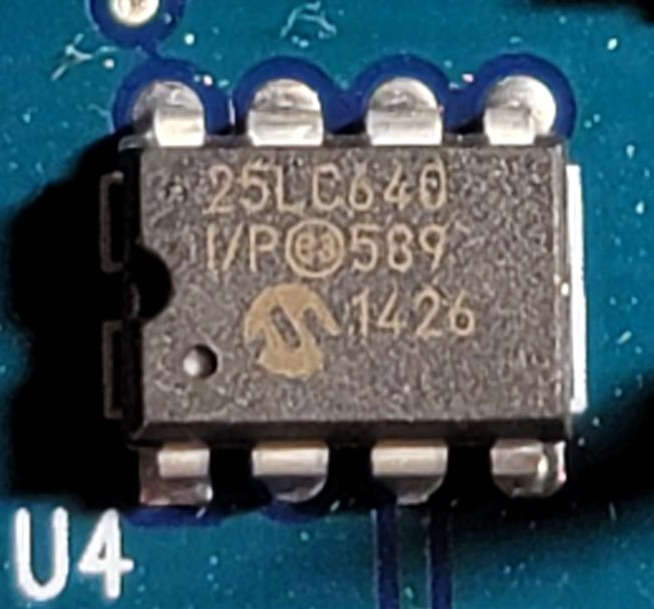
Alarm System Part 2: Security System Teardown
This Blog is part of a Series! Check out the rest if you haven’t already: First things first, it was time to tear out the EEPROM since the reader is coming soon. What You’ll Need Finding PIN 1 This part is important — you can’t take a game cartridge and jam it in backwards because…
-

Decoding USPS PO Box Combinations – Part 2
If you are looking to understand how combination locks work, or you already have access to the inside of a PO Box, you’ll probably enjoy Part 1 a lot more. This one gets into decoding the lock from the outside. Before we start, lets just look at how ornate this damn door is. WOW. So…
-

Decoding USPS PO Box Combinations – Part 1
A few weeks ago I took a trip to a local antique mall here in Texas. It’s been a few years since I’ve been to one and last time was to find old school padlocks to pick. I found this USPS PO Box door (presumably box #60563) for sale for $20, along with several others.…
-
Alarm System Part 1: The old security system
This Blog is part of a Series! Check out the rest if you haven’t already: I’ve recently built my own home security panel. For the code, STLs, and a rambling blog about it, look over here. What does a technology hoarder do with the old system components you probably didn’t ask? I took the existing…
-
Home Security & I’m Back
This Blog is part of a Series! Check out the rest if you haven’t already: I’ve blogged for years on this domain, and every few years I get sick of WordPress or the server I’m hosting on, delete it, and don’t look back. This time is no different. By 2026 or so, this post should…
-

Jackpotting Parking Meters
This post is years old, it was originally posted on my site and was lost for a bit. I’m bringing it back as original as I can, however I do want to mention that this lock is really easy to pick, you just have to be smart enough to try turning the keyway counter clockwise.…
-
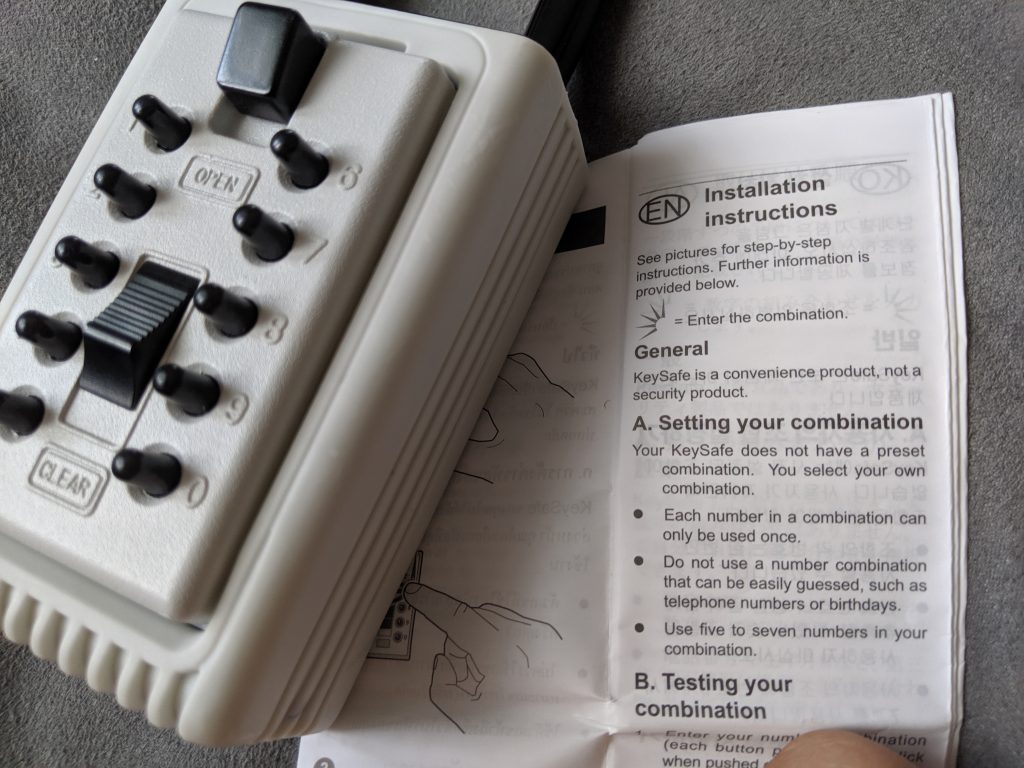
Lockboxes and Key Space Exhaustion
On a rare occasion, I’ll have a chance to check out a thrift shop or antique store and see what sorts of locks or security equipment they have for sale. I’ve wanted to check out those realtor lockboxes for some time, but didn’t want to spring $25 for minimal entertainment value. Today, I stopped in…
-
Cheap Lockpicking Tools
Lockpicking, or Locksport isn’t the most expensive habit to start up. Often times, you have locks laying around (old computers have them, so do old file cabinets, etc). If you’re willing to put in a little elbow grease, you can avoid the expensive tools. Buy a few of the common picks, and tension wrenches, and…
-
Rekeying a Kwikset Deadbolt
Update 2024: This was wrote back in 2019, and while Kwikset SmartKey was around, it wasn’t as common. If you see a small slot next to your keyway, this guide is likely not applicable to you. I’ve been largely an information security-heavy person, I’ve decided that I need to start getting “physical” with physical security.…
-

Stop Using Security Questions
Please stop using security questions. Why security questions were designed with good intentions If you forget your password, a site can ask you a series of security questions. This allows you to recover your account while still potentially authenticating you with questions only you know. Account recovery options are always a great idea, but doing…