Category: Security
-
Overcomplicating Atari Quality Assurance
Atari 2600’s are pretty impressive systems when you consider how many XBox 360’s are RROD’d right now and how many 2600’s are still running. That might be down to simplicity, or maybe engineering! For those of you that don’t know, I’m actively working on building an Atari gamepad with my oldest son. Recently, we took…
-

A Dunce Cap for your Home
This is going to be a bit inflammatory. It’s a different tone than my other blogs. I chose Texas and love living here. But damn y’all. I grew up in the Midwestern United States, lots of agriculture and factories and figuring things out for yourself. The people back home generally view Texans the way Marlboro…
-

Wordfence and a Secure wp-admin
I use WordFence to protect my site from attacks, many years ago I helped a Redditor secure his site (maybe I’ll blog about it one day). He was using WordFence and it found a nasty local file. I’ve enjoyed it enough to where I spoke about it at a security conference a few years ago.…
-

Using AI to Secure Legacy Software
In 2006, I made the decision to stop writing software for Windows (as much as I did at the time), and move to building web applications. The idea was that, unlike desktop applications where I don’t see my users and can’t do updates easily, in a web app I can. I spoke with my brother,…
-
I Messed Up…
Just yesterday, I posted a blog about spying on chip communications. In there, I included a little tidbit that I “deep fried” here. Now, I thought that it was obvious that I was trying to be sarcastic, but today I get an email from my domain registrar telling me that one of my domains has…
-
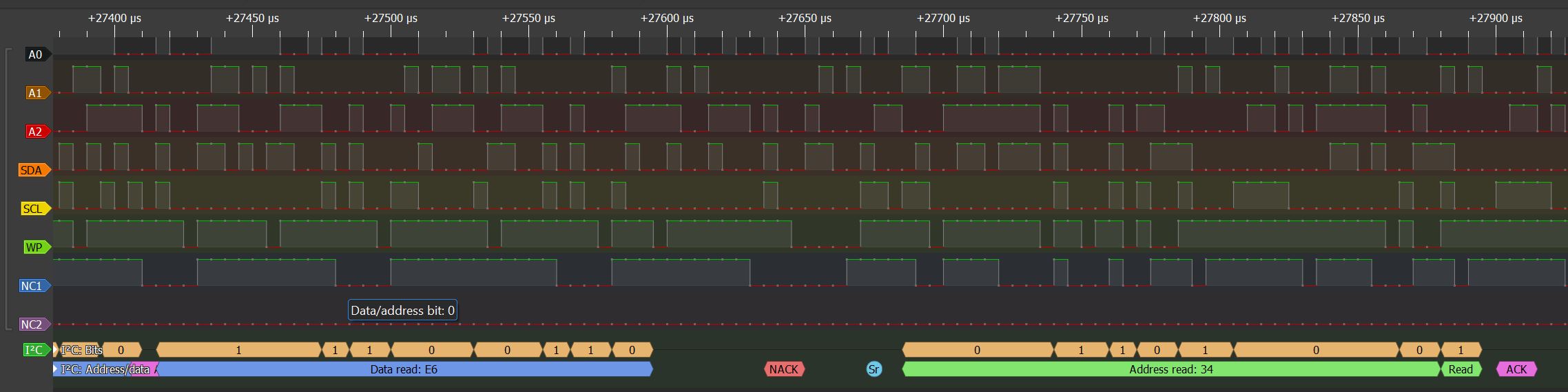
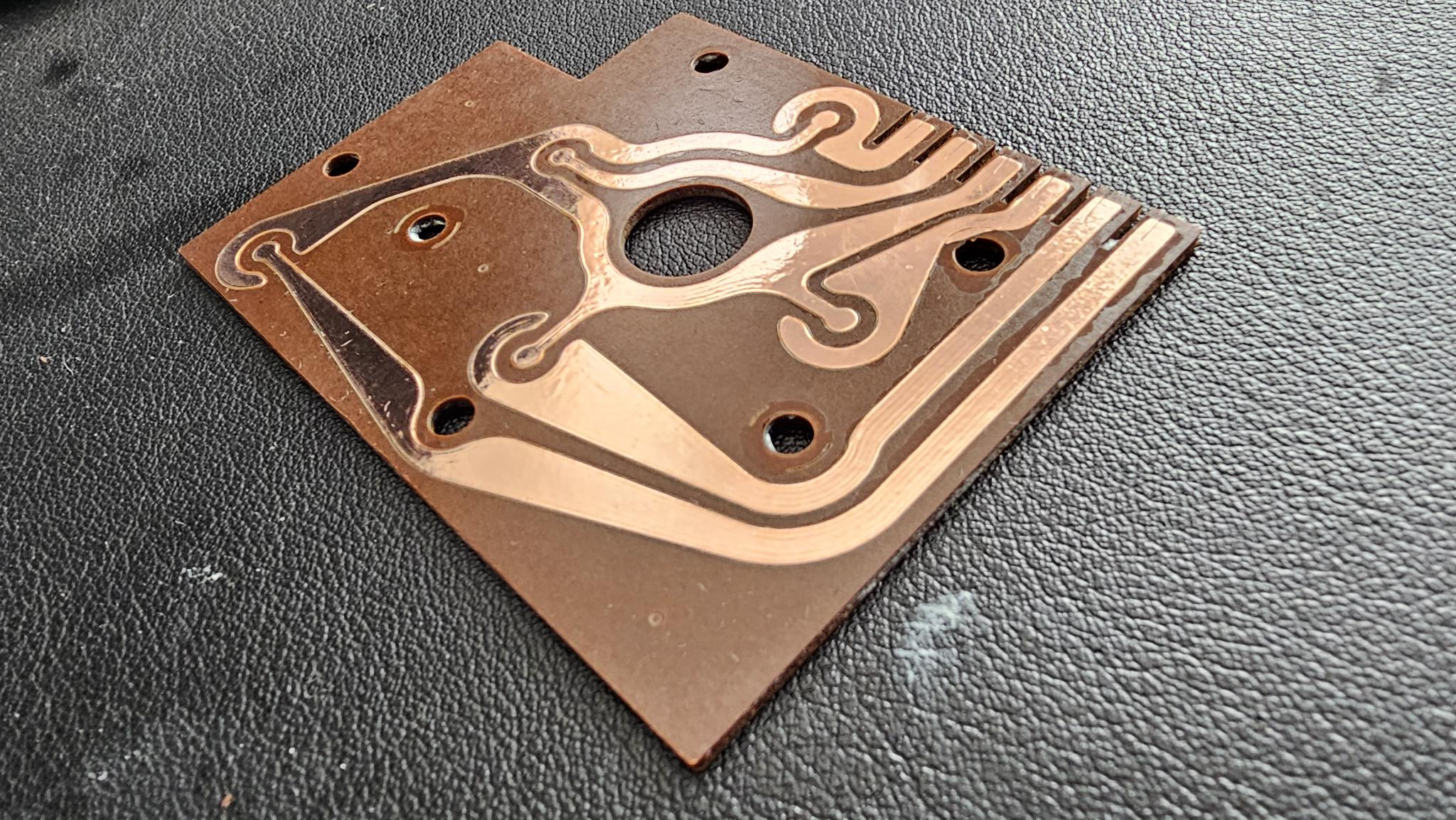
Spying on Chip Communications with Arduino
Recently, I had posted about the faceplate of a safe I had found, got to work, and talked about a method of breaching it. I decided to go a bit further and dump the EEPROM, but the contents of it have (so far) meant nothing to me. I decided it was time to see what…
-

Breaching a Digital Safe
OH LOOK BOB IS GOING TO SHOW US HOW TO USE A MAGNET TO MOVE A SAFE LATCH OR BANG ON IT WHILE PULLING TO HOP A SOLENOID. Not today my friends, but that sure sounds fun, and already done. Most nights, I try to get in a walk. That is, when it isn’t Surface…
-
Lock your Garage Door
It is likely that you lock your front door, your back door, and you use a deadbolt like you should. You may have even invested in a decent quality lock as well. There’s a few items to consider when breaching a home with an attached garage: If you have a garage door opener in your…
-

Be Sure to Drink Your Ovaltine
This year marks the 40th anniversary of The Christmas Story, one of my favorite Christmas movies ever made. I don’t think I’m spoiling anything here since this runs 24 hours a day on a ton of stations in December, but if I am, go watch it first. One scene is especially interesting to folks interested…
-

More Locks = More Security?
This morning, I went for a walk and came upon this rather formidable cell tower enclosure. Usually these things are behind a chain link fence — this one is behind a block wall and has a stout gate. After the 2022 substation attack, I can appreciate seeing stronger protection to critical infrastructure. In this case,…
-

Kroger: A Case Study in Security Theater
Security Theater, simply put, is what you see when you go to the airport, or a court house, or perhaps even your local gas station. A well designed and functional security system should be seen, not used. I would, 100 times over, rather somebody who wants to do me harm, see my security cameras and…
-

Alarm System Part 5: How to Hack a Home Security System
This Blog is part of a Series! Check out the rest if you haven’t already: You read that title. Not “What parts did I order and what struggles did I have” No. “How to hack”, which means we’re damned successful at it, But not so fast. Last I reported, the alarm on a board was…