Category: Software Engineering
-
Arduino as a Clock Source
Quite some time ago, I built a Ben Eater 6502 computer. It was fun but frankly I’m too nervous to do anything cool with it but follow his tutorials. I wanted to take the clock circuit and order a PCB and 3d print a case that allowed me to switch from stepping, astable, bistable, and…
-

Using AI to Secure Legacy Software
In 2006, I made the decision to stop writing software for Windows (as much as I did at the time), and move to building web applications. The idea was that, unlike desktop applications where I don’t see my users and can’t do updates easily, in a web app I can. I spoke with my brother,…
-

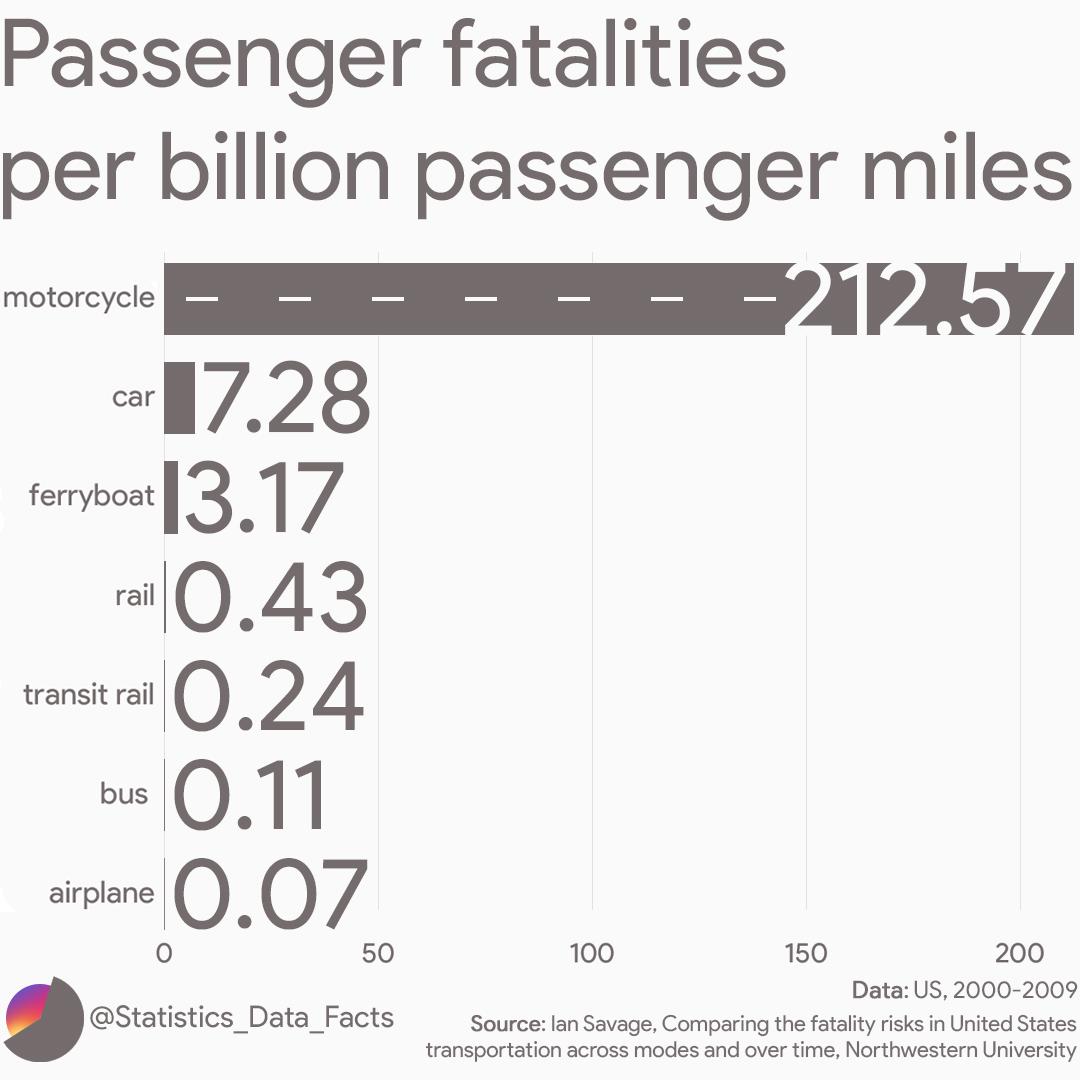
Profiling LMC Assembly Code
What is Profiling? Profiling is measuring the performance of code, whether it is a small function or an entire application. You can determine how quickly the code will execute various requests and tune them to meet your needs. Cycle Counts The Little Man Computer is easy to do math on, it is 1:1 — one…
-

Little Man Computer – Execution
So far, we’ve learned about the Little Man Computer architecture and how to write a simple program and assemble it into machine code. You likely already know how the code is executed due to the high quality comments I’ve included in that blog. Regardless, I built a simulator and spent quite a bit of time…
-
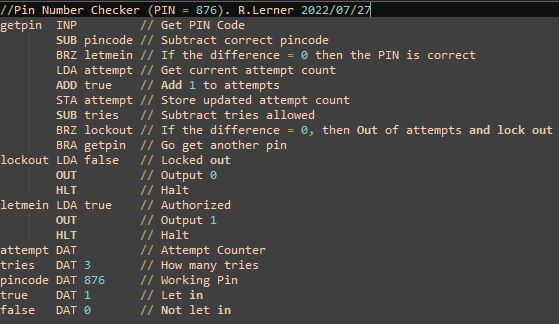
Little Man Computer — Assembly Code
Cover photo isn’t related, but it’s almost as interesting as my post. Machine Code vs. Assembly Code You’ll often hear these two terms used interchangeably, but they are not the same. People will often state that machine code is the actual “0’s” and “1’s” a machine executes, and that’s pretty close to being correct. People…
-
Little Man Computer – Architecture
Around a year ago, I built and threw a Little Man Computer (“LMC”) simulator, assembler, and a really crappy disassembler and put them up on GitHub. There’s another version in C++ up there as well, but it isn’t as fully built out or stable. “Computer Science” in my high school days consisted of keyboarding and…
-

Alarm System Part 5: How to Hack a Home Security System
This Blog is part of a Series! Check out the rest if you haven’t already: You read that title. Not “What parts did I order and what struggles did I have” No. “How to hack”, which means we’re damned successful at it, But not so fast. Last I reported, the alarm on a board was…
-
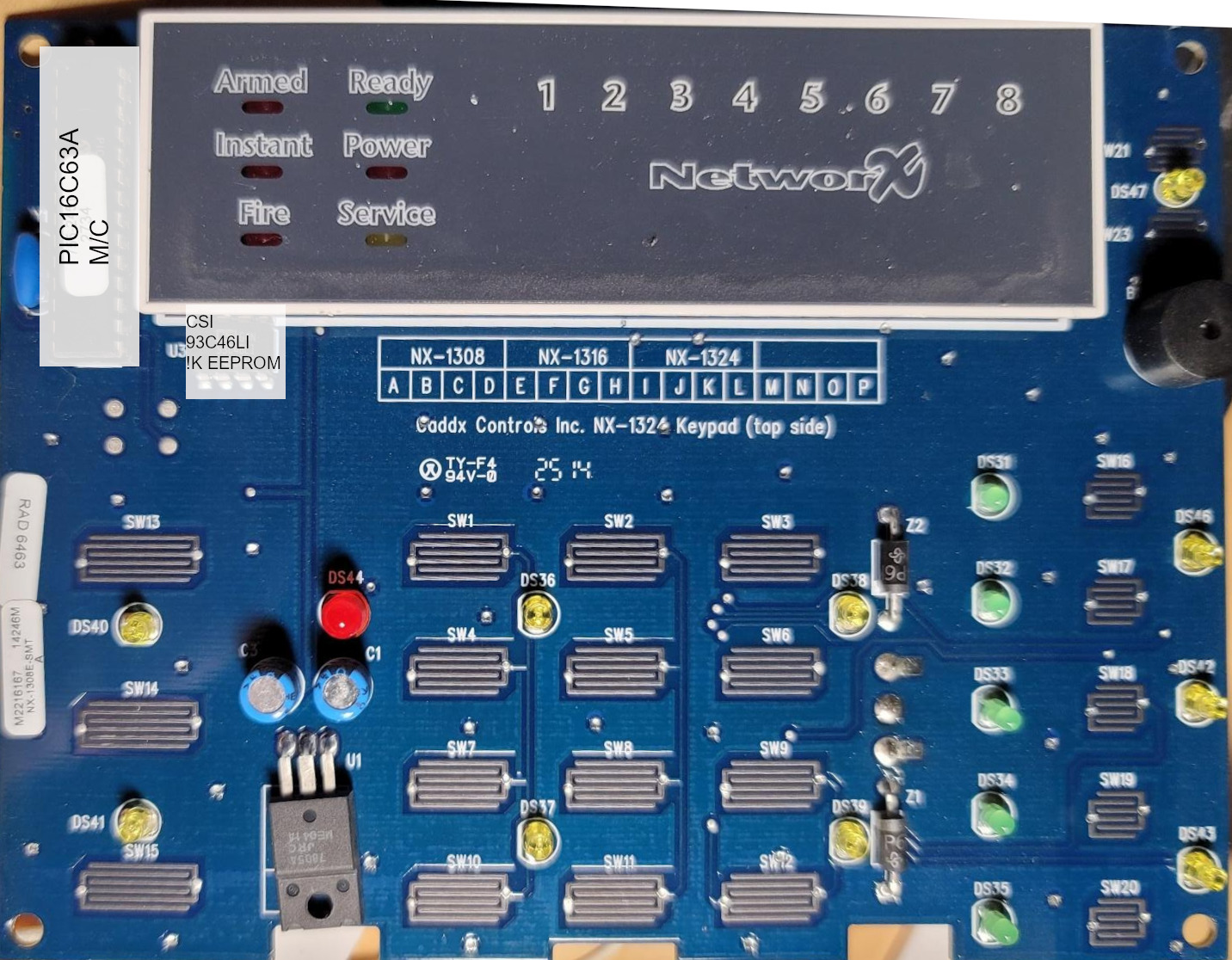
Alarm System Part 4: The Keypad
This Blog is part of a Series! Check out the rest if you haven’t already: At this point, I’ve dumped the EEPROM off the panel, and discovered that there can be some data stored in the PIC Microcontroller on the panel as well. The datasheet for that is >300 pages, so I’m not planning on…
-
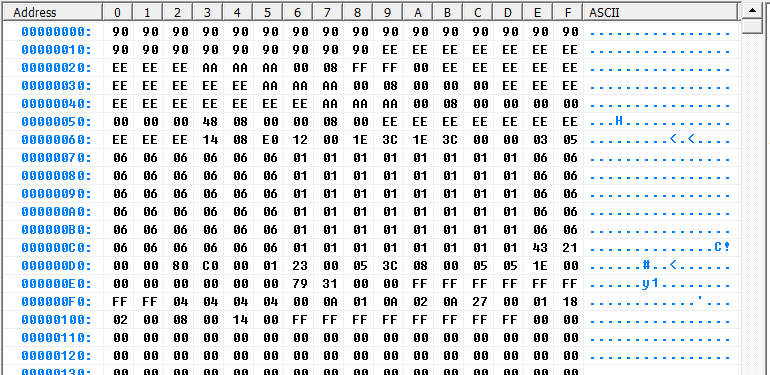
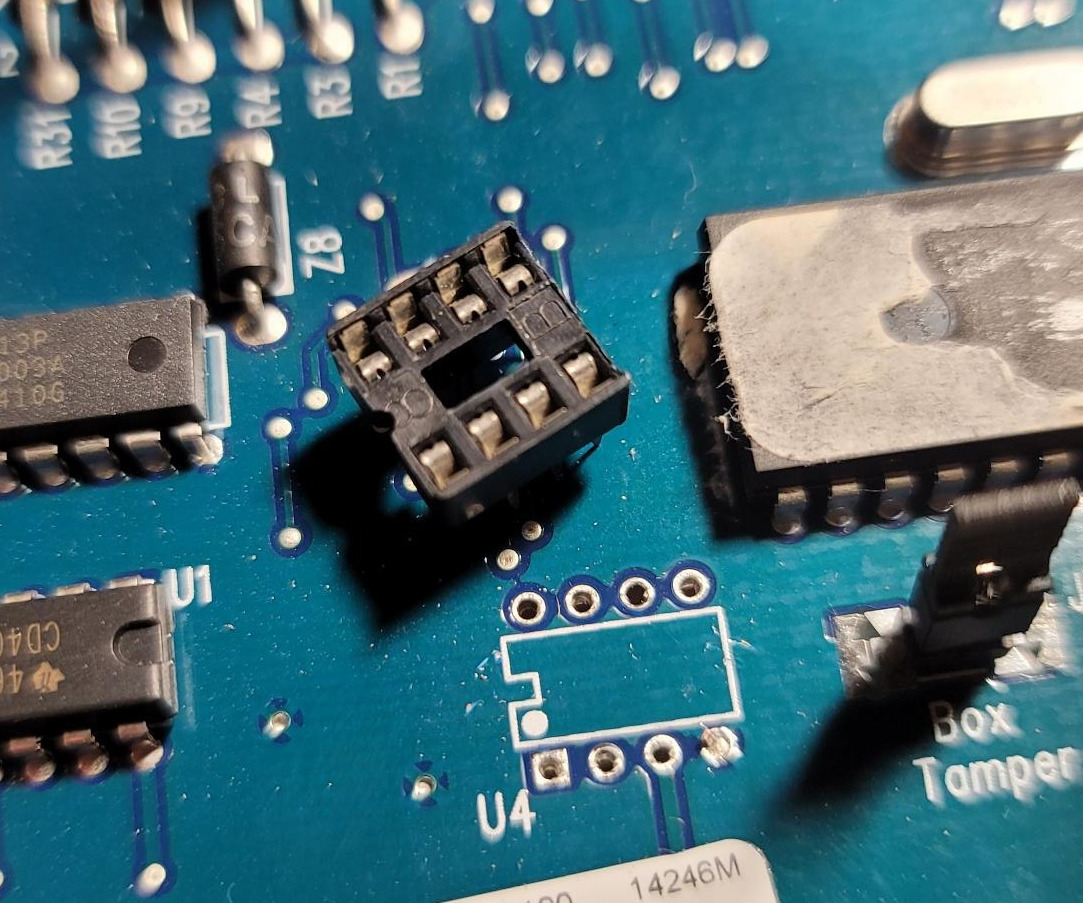
Alarm System Part 3: Security System – Dumping the EEPROM
If you’re coming here looking for the dump, I can’t share it. I don’t know what the laws are on this and it feels pretty DMCA-ish. Sorry. This Blog is part of a Series! Check out the rest if you haven’t already: So, the EEPROM programmer arrived today. For that, I’m excited. And nothing warms…
-
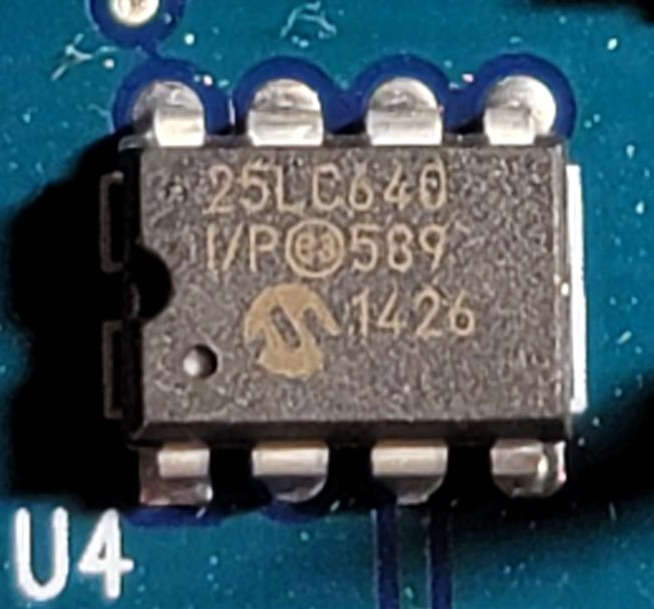
Alarm System Part 2: Security System Teardown
This Blog is part of a Series! Check out the rest if you haven’t already: First things first, it was time to tear out the EEPROM since the reader is coming soon. What You’ll Need Finding PIN 1 This part is important — you can’t take a game cartridge and jam it in backwards because…
-
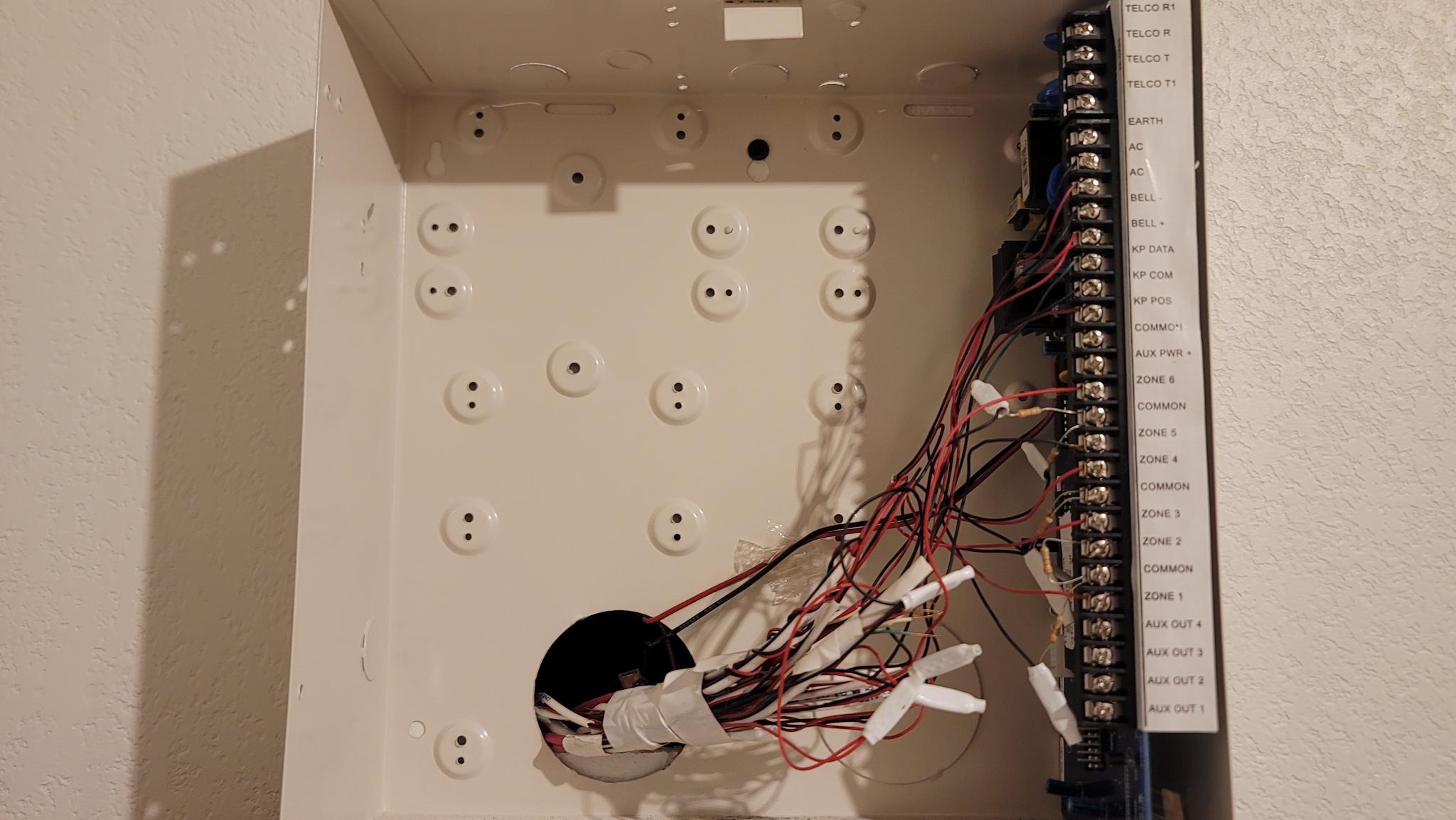
Alarm System Part 1: The old security system
This Blog is part of a Series! Check out the rest if you haven’t already: I’ve recently built my own home security panel. For the code, STLs, and a rambling blog about it, look over here. What does a technology hoarder do with the old system components you probably didn’t ask? I took the existing…
-
Home Security & I’m Back
This Blog is part of a Series! Check out the rest if you haven’t already: I’ve blogged for years on this domain, and every few years I get sick of WordPress or the server I’m hosting on, delete it, and don’t look back. This time is no different. By 2026 or so, this post should…