I use WordFence to protect my site from attacks, many years ago I helped a Redditor secure his site (maybe I’ll blog about it one day). He was using WordFence and it found a nasty local file.
I’ve enjoyed it enough to where I spoke about it at a security conference a few years ago.
So I was a bit surprised when I logged in today and seen that my scan are failing
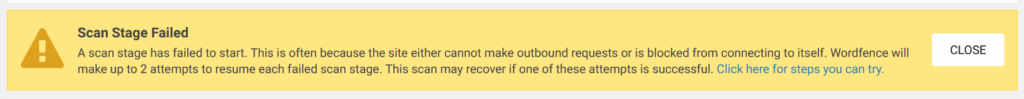
Clicking on the “Click here for steps you can try” link took me here. One of the issues it mentioned was when you lock down /wp-admin/ (gasp, I use WordPress).
This immediately stuck out to me since I had locked access to it to only my local IP back when my pal at work Zach (HackAttackZack) decided to kick off a few DAST scans against my site and I locked stuff down.
Thankfully, it’s an easy fix. I added the IPs listed to my directory lockdown and it began working immediately:
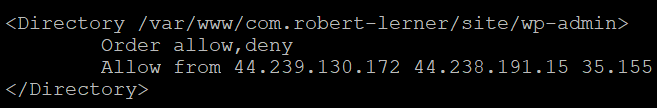
Zomg Directory Structure.
Short blog, easy solution. Note that the WordFence people state that locking down wp-admin also breaks AJAX for users not in the IP list, but I haven’t heard any complaints (MAYBE MY COMMENT FORM IS BROKEN?!?!?) jk it isn’t.
Ajax is a cleaning agent anyway.

Leave a Reply