Author: rlerner
-

Phantom of the Opera Ornament Repair Part 2
This is crazy. Most of the blogs I post with “parts” never see a final “part” because I get bored, go to another task, etc and backburner it. Finally, this one is “done”. That said, most of the meat here is over in Part 1… So read that first. The goal I left off on…
-
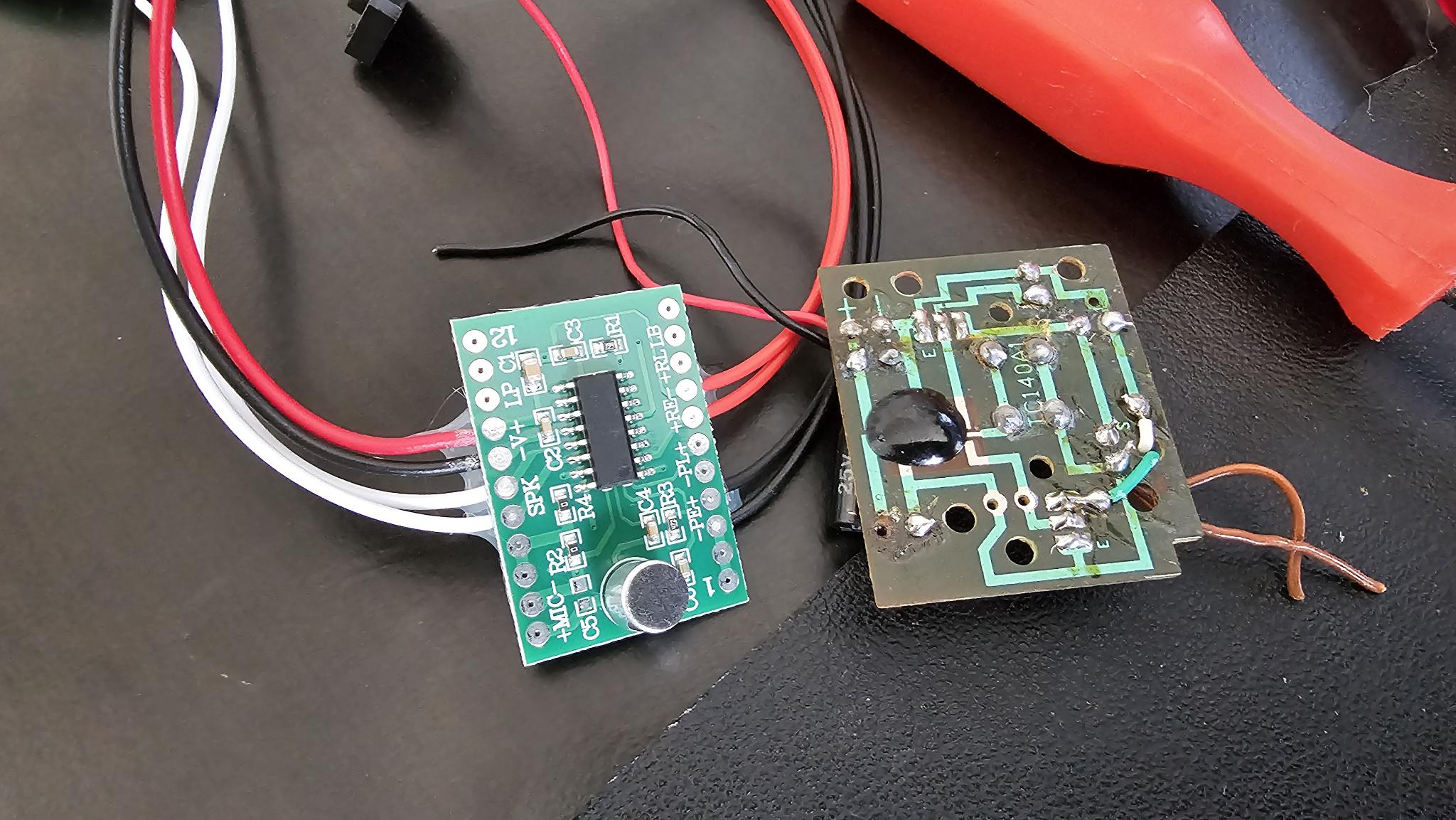
Phantom of the Opera Ornament Repair Part 1
My mother in law was in town and took my wife shopping for her birthday at an antique mall here in town. They stumbled upon a Carolton Cards Phantom of the Opera ornament from 1999 that my wife loved. Other ones were selling for $300 (note there are a few different years and styles, and…
-

Jailhouse Wine Time
Why Jailhouse wine? Without being to either, I would imagine jail is an upgrade from prison, and while I made prison wine using just grape juice and bread yeast, I think that the folks who are in temporary custody might have access to better ingredients, like aging oak, specialty strains of yeast, and better juice…
-
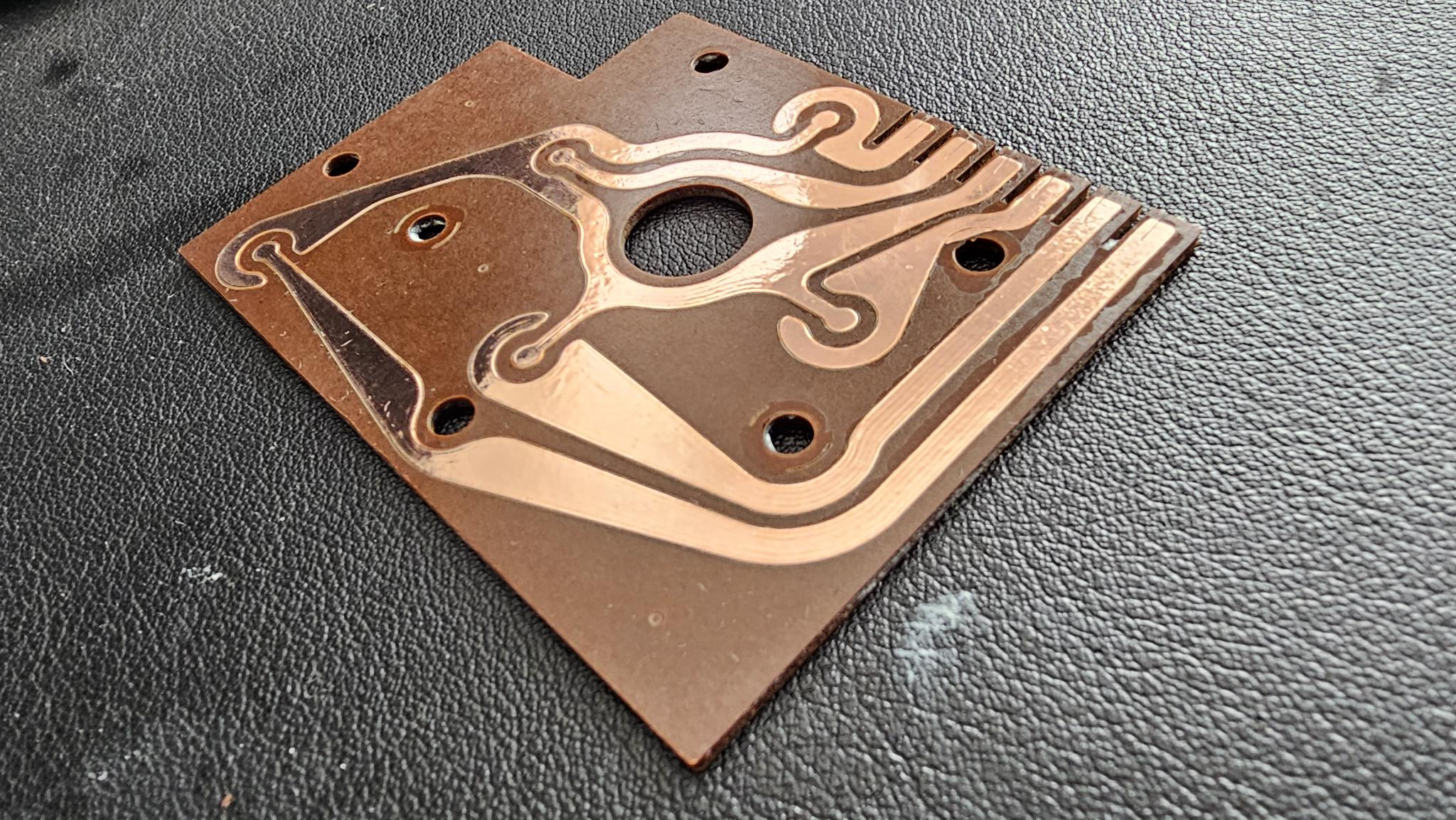
Overcomplicating Atari Quality Assurance
Atari 2600’s are pretty impressive systems when you consider how many XBox 360’s are RROD’d right now and how many 2600’s are still running. That might be down to simplicity, or maybe engineering! For those of you that don’t know, I’m actively working on building an Atari gamepad with my oldest son. Recently, we took…
-

A Dunce Cap for your Home
This is going to be a bit inflammatory. It’s a different tone than my other blogs. I chose Texas and love living here. But damn y’all. I grew up in the Midwestern United States, lots of agriculture and factories and figuring things out for yourself. The people back home generally view Texans the way Marlboro…
-

Learn How to Redacted Drive! Part 1
If you already know what an acceleration lane is, don’t go ahead and skip this. I’ve been behind you and I know damn well you have no idea what the hell I’m talking about. Why am I the authority on driving? Let me share my credentials: Now that we got that out of the way,…
-

Manufacturing an Atari Gamepad, Part 1
If you’ve played the 2600, you probably thought it was the greatest thing in the world, but those rose colored glasses likely fell the first time you picked up something even as simple as an original NES controller. The joysticks that come with the Atari have this large rubber boot on the bottom: When you…
-

Fixing an Atari 2600 Cartridge
One of my sons are homeschooled, and while he’s a bit young to understand assembly, or building his own computer, or writing his own Atari games — I can start with the fundamentals. What a better system to learn about computers than a game system, and one so simple that the component count is incredibly…
-

My Most Useful Blog
I didn’t come up with this, I read it somewhere or seen it in a video. Regardless, more people need to do this. If you drop small stuff on the floor constantly like I do, don’t look around and the floor OR shine a flashlight directly away from your eyes — instead, sweep the beam…
-
Arduino as a Clock Source
Quite some time ago, I built a Ben Eater 6502 computer. It was fun but frankly I’m too nervous to do anything cool with it but follow his tutorials. I wanted to take the clock circuit and order a PCB and 3d print a case that allowed me to switch from stepping, astable, bistable, and…
-

Powering Up Christmas: A Creeper Clock Makeover
If you aren’t comfortable around electricity, don’t attempt this. Consult a professional. Make sure nothing is plugged in. Doing this may impact the warranty of the device or prevent the resale of the device. It feels like the plethora of garbage you can buy on Amazon is just designed to sell more USB power bricks…
-

3D Printing a Microphone
A few weeks back, a friend was over for some prison wine. We decided we’d karaoke and have a good time, but I was having an issue finding a microphone. I had casually remarked “Well, I’ll just go 3d Print one”, and he said “There’s no way, right?” and I replied “Of course not!” Challenge…